Author: chris
-
What is the Faculty Bearometer
The Faculty Bearometer is a one-question survey posed to the Senate Faculty on issues of teaching and governance. Read more about it here.
-
Bearometer 1: Welfare
On January 27th, 2025, we distributed the following question to senate faculty (2635 members) via Qualtrics email contacts. 300 submitted responses. What is the single most important challenge to your overall welfare as a faculty member at Cal? Results are at the link circulated to senate faculty members.
-
What is the Faculty Budget Forum (FBF)?
The Faculty Budget Forum is Berkeley largest email list for faculty-to-faculty interaction on governance matters.
-
Fundamental Challenge: Strategy
Understanding our terminal goals is the core challenge of governance. Our terminal goals are to have world-class research and excellent teaching. Our governance activities should focus on promoting these strategic goals, and limiting the effects of other goals on these strategic goals. It’s easier for me to get reimbursed by stodgy European universities, where I…
-
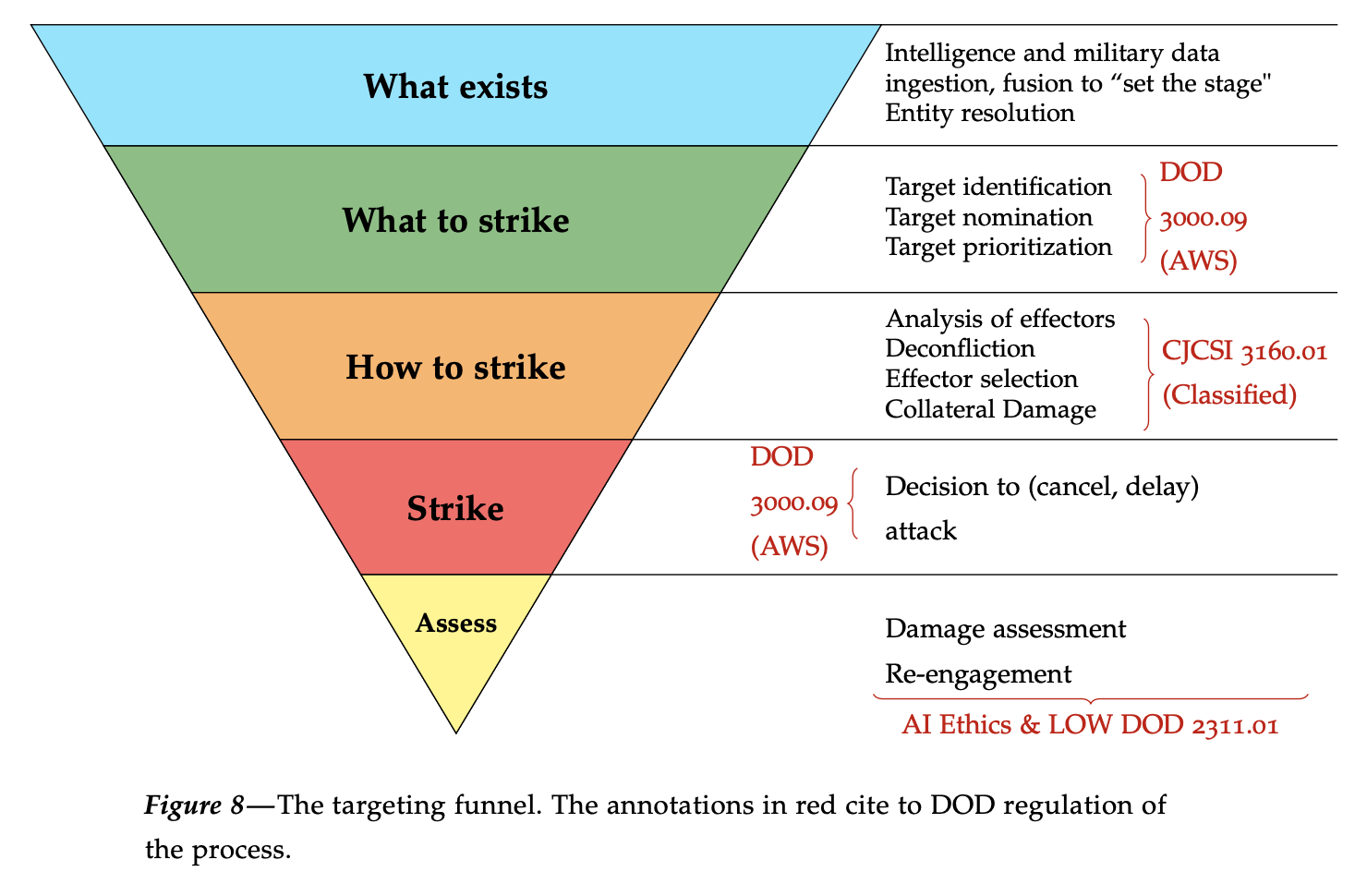
How the AIs Kill
Are we on the precipice of developing autonomous killer robots; unmanned technologies that will completely dominate conflict, remorselessly, perfectly? Some advocates think so but this article explains why the killer robot view is misplaced and in its misdirection, draws attention away from how militaries already use artificial intelligence and machine learning technologies. The article draws…
-
Proposed Principles for Policy Evaluation
All senate committees should consider this framework for policy analysis.
-

Cybersecurity in Context
Cybersecurity in Context is forthcoming from Wiley September 2024! Pre-order here. Every one now has a stake in the healthy functioning of communications and control networks, in the devices and services dependent on network, and by implication, in all the complicated infrastructure required to keep networks, devices, and services operating. As we have become more…
-
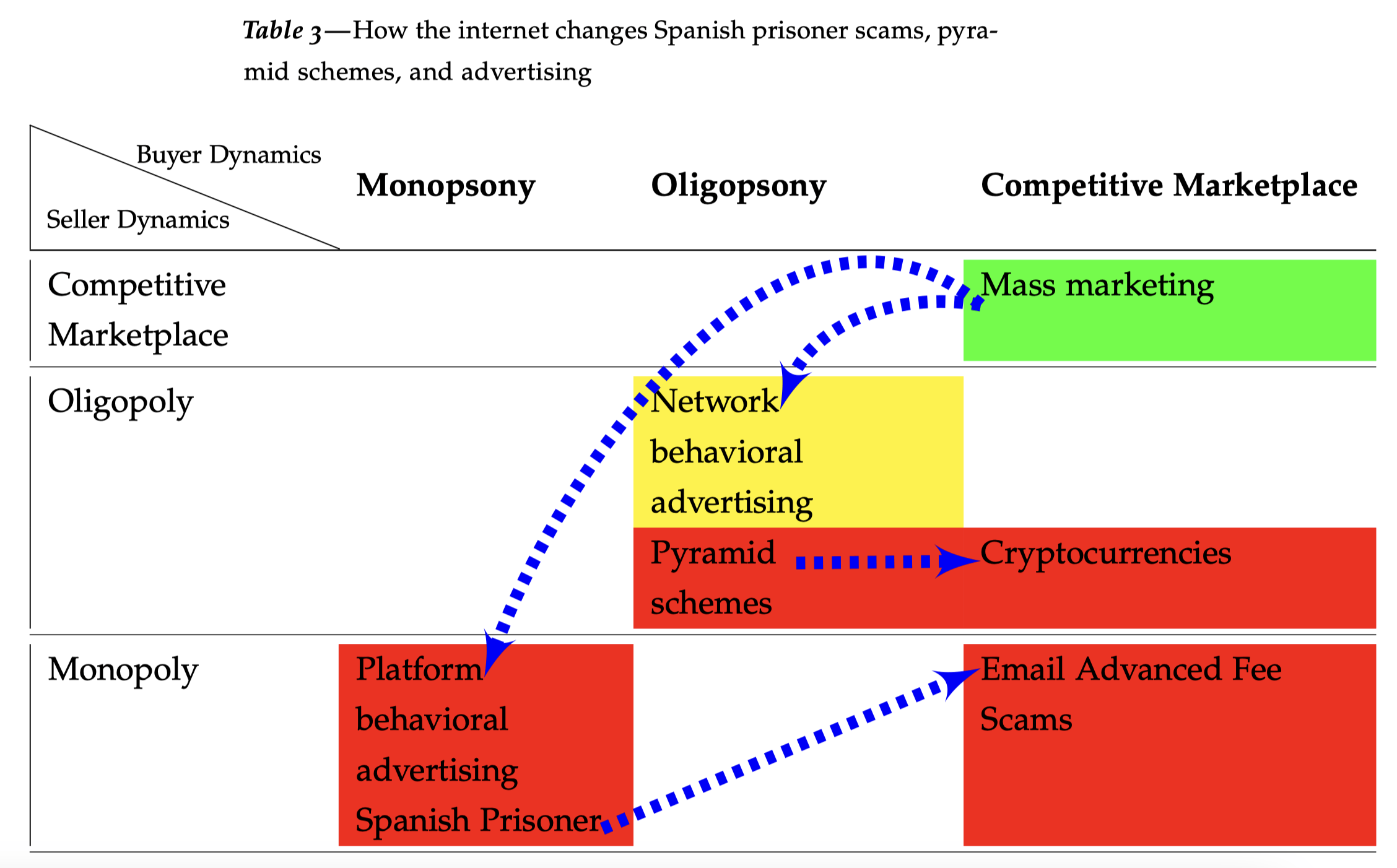
The Techcons
Revisiting Arthur Leff’s Swindling and Selling Published as Chris Jay Hoofnagle, The TechCons, 37(1) Loy. Consumer L. Rev. 1 (2025)(Hein)(local) Yale Law Professor Arthur Leff wrote a powerful, market-structure analysis of consumer fraud in his 1976 Swindling and Selling. That work is more or less lost to history. Leff explained that con artists attempted to impose…
-
Cybersecurity in Context
New course: Fall 2024! In fall 2024, I will teach Cybersecurity in Context in the Legal Studies program (LS 190). The course will be based on my new textbook with Golden G. Richard III. Course Description Cybersecurity has become instrumental to economic activity and human rights alike. But as digital technologies penetrate almost every aspect…
-
Cybersecurity Courses @ Cal
A growing number of faculty are offering cybersecurity courses at Cal. Consider taking: The Center for Security in Politics offers a graduate certificate in security policy. Many of the electives are open to undergraduates. They include GSPP PP 155/255 Introduction to Security Policy (Professors Janet Napolitano and Daniel Sargent) PPC285 and NUCENG 285C Nuclear Security: The…
-

Computer Programming for Lawyers
Most recent syllabus: Spring 2023. Clients increasingly want their lawyers to understand their products and services on a technical level. Regulators need to understand how their rules will be implemented in code. Lawyers increasingly need tools to automate the process of collecting, organizing, and making sense of impossibly large troves of information. Computer Programming for…
-
Torts (1L)
Welcome to your first year of law school and to torts, a topic as rich as it is traditional in legal education. Torts provides an expansive lens to learn about the American legal system. This course will cover the basics of torts and in the process, the fundamental reasons and principles underlying doctrine. Learning Goals:…