Chris Jay Hoofnagle is Professor of Law in Residence at the University of California, Berkeley, School of Law, where he teaches cybersecurity, programming for lawyers, and torts. He is affiliated faculty with the Simons Institute for the Theory of Computing and the Center for Security in Politics. In Spring 2024, Hoofnagle visited King’s College Department of War Studies.
Hoofnagle’s new book with Golden G. Richard III is Cybersecurity in Context (Wiley 2024). Previous works include Law and Policy for the Quantum Age (with Simson Garfinkel, 2022) and Federal Trade Commission Privacy Law and Policy (2016), both with Cambridge University Press.
An elected member of the American Law Institute, Hoofnagle is of counsel to Gunderson Dettmer LLP, a longtime advisor to Palantir Technologies, and a member of the National Academies Intelligence Science and Technology Experts Group (ISTEG).
With Professor Daniel Solove, Hoofnagle founded the Privacy Law Scholars Conference.

In-progress works
-
The EU Cybersecurity Framework: What it is, What it Means
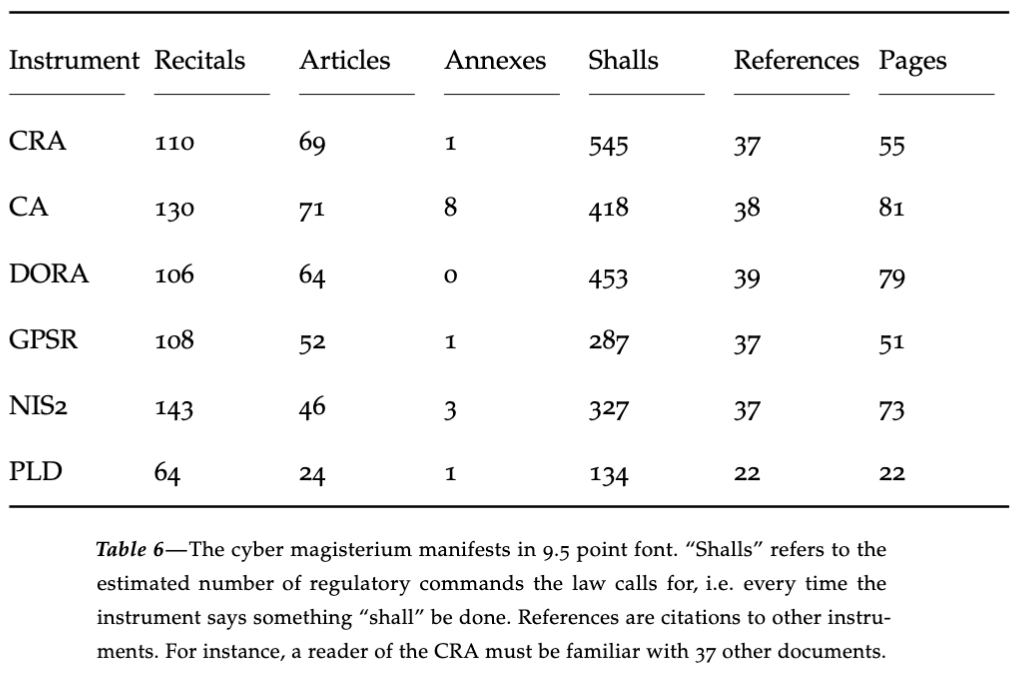
If your clients develop standalone software or connected products, they need to know about the European Cybersecurity Framework. Enacted with little public attention, the Framework imposes far-reaching obligations on developers of standalone software and connected products. It establishes a stringent software product liability regime with rigorous security requirements and no meaningful small-business relief. In many…
-
How the AIs Kill
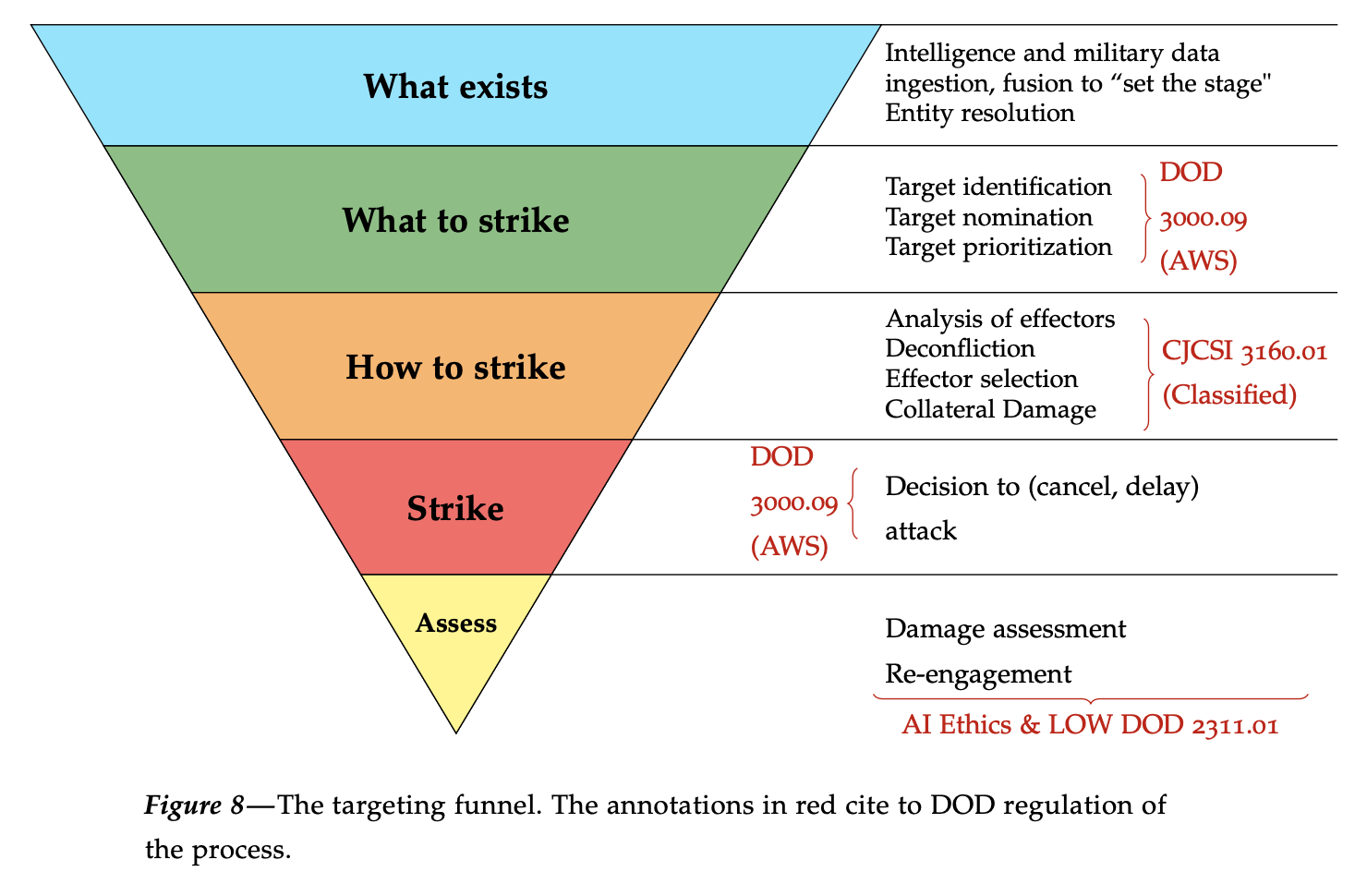
Are we on the precipice of developing autonomous killer robots; unmanned technologies that will completely dominate conflict, remorselessly, perfectly? Some advocates think so but this article explains why the killer robot view is misplaced and in its misdirection, draws attention away from how militaries already use artificial intelligence and machine learning technologies. The article draws…
Publications
h-index: 33, i10: 44

Quantum Cryptanalysis: Hype and Reality Journal Article
In: Lawfare: Hard National Security Choices, 2022.

Law and Policy for the Quantum Age Book
Cambridge University Press (Open Access Published), 2022.

The Apple Privacy Debate: Scanning Photos Is in Service of `Human Freedoms’ Journal Article
In: Future of Sex, 2021.

Fighting Insider Abuse After Van Buren Journal Article
In: Lawfare: Hard National Security Choices, 2021.

The European Union general data protection regulation: what it is and what it means Journal Article
In: Information & Communications Technology Law, vol. 28, no. 1, pp. 65–98, 2019.

The Federal Trade Commission’s Inner Privacy Struggle Book Section
In: Selinger, Evan; Polonetsky, Jules; Tene, Omer (Ed.): The Cambridge Handbook of Consumer Privacy, pp. 168, Cambridge University Press, 2018.
Facebook and Google are the new data brokers Journal Article
In: Cornell Digital Life Initiative Critical Reflections, 2018.

Designing for Consent Journal Article
In: Journal of European Consumer and Market Law, vol. 7, no. 4, pp. 162–171, 2018.

Facebook in the Spotlight: Dataism vs. Personal Autonomy Journal Article
In: JURIST – Academic Commentary, 2018.

Sponsored Blog Content: What Do the Regulations Say: And What Do Bloggers Say Journal Article
In: J. Intell. Prop. Info. Tech. & Elec. Com. L., vol. 9, pp. 146, 2018.
Deterring Cybercrime: Focus on Intermediaries Journal Article
In: Berkeley Technology Law Journal, vol. 32, no. 3, pp. 1093, 2017.
For a list of research organized by research theme/question, click here.
Teaching
Governance
Berkeley has big problems with governance. I have a hypothesis of what has gone wrong and what to do about it.
-
Comments on Sustainability, Round 2
Thank you for the opportunity to comment on the proposed revisions to the University of California Policy on Sustainable Practices. I share the University’s commitment to environmental stewardship. My comments focus not on the aspirations of the policy, but on questions of scope, prioritization, cost, and institutional capacity, issues that I believe warrant fuller consideration…
-
Norms as Ontologies: Berkeley’s Virtue Signaling with Externalization
One of the things I treasure most about Berkeley is the sincerity of its community. As a public university, Berkeley aspires not merely to produce knowledge but to foster civic virtue. Our official statements are filled with values I share: equality, stewardship for the environment, belonging, accessibility, justice. These are noble commitments. They form part…
-
What is the Faculty Bearometer
The Faculty Bearometer is a one-question survey posed to the Senate Faculty on issues of teaching and governance. Read more about it here.
-
What is the Faculty Budget Forum (FBF)?
The Faculty Budget Forum is Berkeley largest email list for faculty-to-faculty interaction on governance matters.
-
Fundamental Challenge: Strategy
Understanding our terminal goals is the core challenge of governance. Our terminal goals are to have world-class research and excellent teaching. Our governance activities should focus on promoting these strategic goals, and limiting the effects of other goals on these strategic goals. It’s easier for me to get reimbursed by stodgy European universities, where I…
-
Proposed Principles for Policy Evaluation
All senate committees should consider this framework for policy analysis.
-
The Reducing Bureaucratic Burden Report
The July 2023 “Reducing Bureaucratic Burden Task Force Final Report” [perma.cc link] is a critical read to understand governance, but many faculty don’t know about it. The full text is reproduced below. Reducing Bureaucratic BurdenTask force final report July 7, 2023 Task Force MembershipMaximilian Auffhammer, Professor, Vice Chair of the Academic Senate (co-chair) Andrea Lambert-Tan,…
-
Questions for the Vice Chancellor for Administration
In my opinion, some of Berkeley’s biggest problems emerge from the VCA’s portfolio.
FAQs
What is TLW—the Technology for Lawyers Workshop?
Technology for Lawyers Workshop (TLW) is a self-paced, two-session workshop covering the computer skills most important to success in law school.
By working along and doing the exercises, you’ll become a more efficient user of your computer, and in the process, develop templates you can use for law school assignments.
Session 1 is 40 minutes long, and it focuses on your computer generally and clever uses of the Web.
Session 2 is a deep dive into Microsoft Word. In this session, you will learn how to make proper templates for your legal writing. The session is 90 minutes long.
You can self-enroll here: https://bcourses.berkeley.edu/enroll/YCXH8X
Will you serve on my quals or PhD committee?
Maybe! I am a senate member and member of both the law and information faculties, so I can serve as an outside member in many configurations. Please email me a description of your research agenda, and how you think my participation will benefit your research.
I will not pay attention to a QE or other proceeding on Zoom. Sorry.
I\’ve heard about your plantar fasciitis tricks…
Yes, plantar fasciitis is super annoying. Years ago, I found a literature review (can’t find it anymore) that suggested that all interventions for plantar fasciitis were equally inefficacious, and it is a condition that takes about 18 months to heal. Ouch! Furthermore, my foot doctor told me that surgery alleviates the pain but undermines the strength of your foot.
But I discovered a few tricks:
- These boots that one wears overnight to keep your foot tensioned work quickly to alleviate acute pain. Don’t use the sock ones. Use the full size one that looks like a plastic cast for a broken foot. Don’t over tighten it. Just use it so that your foot is angled slightly more than 90 degrees. If you can’t sleep with it, the boot is probably too tight or too aggressively angled.
- Voltaren, a “arthritis pain reliever,” now available over the counter-generic as diclofenac gel, is a godsend. They key is that you can put it on your foot and avoid the digestive complications from oral anti-inflammatories. Voltaren got me running in less than a week.
- Some sports, because of how your foot is angled, do not aggravate the plantar fascia. For instance, downhill skiing is great—your foot is stretched by the ski boot, making it almost like an hours-long treatment. Similarly ice skating does not aggravate my fascia even if done for hours. So you can keep in shape.
- I’ve found that the elliptical trainer doesn’t aggravate plantar fascia, and so you can do it for hours without injury. Don’t buy a cheap elliptical, they’re junk. Don’t trust the reviews either. You need to spend over $1k. The Sole E35 is a solid choice. But my favorite elliptical is the Octane XT and Q series standing ellipticals, which have stride lengths over 20 inches. You can find them on Craig’s List. I bought one used from a commercial gym for about $1k.
- Watch out for watches! I got a new Garmin watch, and it nudged me to run long and longer. I found myself running 10ks every other day, and then ended up with plantar again, putting me back at 2 mile runs…
Don’t overdo it. When I feel pressure in my heel, I know I am close to injuring my plantar fascia. So, for me at least, this is a permanent running injury 🙁
How do you contribute to DEI at Berkeley?
Technology law as a field is not known as being particularly diverse, nor inclusive. In my career at Berkeley, I have taken specific, sustained action to promote women in higher education, to raise awareness of SES issues in technology, and to include underrepresented and minority students in my work. Come by my office hours and I can speak with you in greater detail about these efforts. I’d also love to hear your thoughts about how BCLT can address systemic inequalities.
Recent events have caused me to deepen diversity and inclusion efforts in teaching. I plan to devote more classroom time to the structural causes of exclusion and inequality. For instance, in my technology courses generally, I intend to connect students with the history of Silicon Valley, and the root causes that made the area and its most successful companies homogenous. Few people know that Lockheed was the largest employer in the Valley until the rise of the .com bubble. Lockheed and other defense industrial base companies were male and white dominant (Lockheed was 85% male and 90% white even after equal opportunity laws were enacted). The demands of secrecy surrounding the DIB, the military R&D subject matter, and other factors caused systematic exclusion since the 1940s. Thus, when we think about inclusion in tech today, we have to contemplate addressing decades of disadvantage.
Confronting inequality is also a key element in my pure doctrinal courses, such as torts. I use the Witt/Tani casebook because it starts by situating the institutions of torts, because it explains how key doctrines compensate women and minorities and the poor differently, and because many of the cases selected by Witt and Tani have clear social class or race dynamics. Traditional cases that never received a class analysis—from Vosburg to Palsgraf—are recast in their casebook. My aim is to arm students with these insights so they can critically discuss the tradeoffs and implications of legal policies that promote formal equality or substantive equity.
Where can I find Berkeley Old Style Fonts?
What is the Faculty Budget Forum (FBF)?
The Faculty Budget Forum (FBF) is an email list of about 400 Berkeley faculty members. It is among the largest lateral (department to department) lists we have—the other being Teach-Net. If you are a faculty member, I am happy to add you to FBF. Just email me.
Will you supervise my JSP or JSD (PhD in law)?
Maybe! It is a delight to have a multi-year collaboration with JSP and JSD students. But JSP and JSD degrees require serious commitment because the point is not just for you to learn, but for you to make a new contribution to the literature. When you write your purpose statement, it’s not enough to just identify a topic. You must drill down and identify:
- The intellectual ideas that you want to engage in
- The literature surrounding your proposal, and how your investigation will answer problems not yet explored adequately
- Ideas that are “big enough” to justify a multi-year exploration
- Ideas that are important enough to justify the exploration—after all, you are going to spend years of your life on it 🙂
- The reasons why Berkeley is the right place for this exploration (what faculty/departmental/institutional characteristics of Berkeley are a good match for you)
- The training/experience you have that will make you successful in the research journey
Whom have you mentored at Berkeley?
Despite teaching in a professional program, I’ve had the chance to mentor some graduate students, including:
- Shazeda Ahmed, Berkeley PhD
- Zehra Betul Ayranci, Berkeley PhD, Fox Sports
- James Carney, Joanne Jia, Archana Kulkarni, Cameron Lopez, PrivacyBot Capstone Project (Information)
- Ella Corren, JSP
- Amit Elazari Bar On, head of global cybersecurity, Intel
- Gal Forer, JSD
- Kevin Frazier, USD Law
- Alexi Pfeffer-Gillett, UMD Law
- Grace Gordon, Master of Development Practice
- Arianne Jimenez, Privacy and Public Policy Manager Facebook APAC
- Aniket Kesari, Yale/Berkeley JD/PhD, Fordham Law
- Irene Kamara, Standardising data protection: a European perspective in an interconnected world, Tilburg University (Netherlands)
- Sam Kumkar, EECS
- Morgan Livingston, ISF
- Sylvia Lu, Law
- Rachna Mandalam, ISF
- Nicole van der Meulen, EC3
- Andrew Reddie, UC Berkeley
- Nikita Samarin, EECS
- Ankeet Shankar, Capstone Project (Information)
- Bart van der Sloot, Tilburg University
- Ashkan Soltani, privacy/security researcher
- Eric Winkofsky, JSD
In addition to these students, with Dean Shankar Sastry, I was Co-PI of a program (TRUST SITE REU) with a goal to increase diversity in graduate STEM programs. We hosted scores of undergraduates at Cal, and in some cases, I published papers with these students, including Mika Ayenson (Johns Hopkins University Applied Physics Laboratory), Shannon Canty, Quentin Mayo, and Lauren Thomas.
I\’m a prospective student, will you…?
Apologies, I generally do not meet with students unless they are admitted to a program. Similarly, if you are a student at another program, apologies, I cannot supervise or give you advice on your research.
Please know that admissions at Berkeley is handled by a committee and that I have no influence over decisions.
What is your role with the academic senate?
I ran for the UCB Divisional Council in 2022 and won election for the 22-23, and 23-24 years. Known as DIVCO, the body could be thought of as the executive arm of Berkeley’s academic senate. I ran because of concerns about campus priorities and the strategic challenges we face. Berkeley is facing macro constraints including costs of housing and living in the Bay Area that are steadily eroding our competitive posture, and at the same time we lack features that help institutions perform (biggest example: no medical school).
We should be thinking big, with eyes on a 2030–2040 horizon. Some of the ideas I think are worth pursuing include: creating faculty housing like that offered at NYU and Colombia, creating student housing close to campus—even using eminent domain to reform the sleepy properties that surround the campus, rethinking how much of our central campus is devoted to sports infrastructure, building a medical school, and developing campus institutions that can more competitively interact with D/I/H-ARPA.
We should fundamentally rethink how we can use campus resources to compete for and retain faculty. Other schools use campus resources to provide perks for faculty that we simply don’t consider. For instance, we have a fantastic eye clinic at Berkeley—why won’t we offer corrective vision surgery as a retention strategy, or as a privilege connected with earning tenure, or even as a recruitment tool for the best graduate students?
I also ran because in my opinion, Berkeley gets in its own way too often. We literally decide not to do “the right thing” or the strategic thing because of transaction costs we have imposed upon ourselves. We are becoming more process-based and managerial. Just as employees adopt “shadow-IT” to circumvent bad technology decisions, some faculty employ shadow-operations to get their work done.
Senior faculty members spend much of their time now on process and paperwork. We need to formally declare a time-value to faculty member time, and eliminate rules, trainings, and paperwork that 1) excessively impose upon faculty time or 2) are not risk-justified. From reimbursements to CPHS to IACUC to even the merit review process, we have no evaluative method that acts as a ceiling on paperwork and faculty time and we don’t probe the upside/downside risks from process requirements.
Candidate Statement
My governance experience at Cal includes campus-level (CPHS, leading the Center for Long Term Cybersecurity, developing a professional masters in cybersecurity, Senate academic freedom committee) and school-level service (HGA of our cyber program, building space, admissions). I am a former member of the AAUP’s Committee A on Academic Freedom and Tenure and helped it develop policy on protection of electronic communications. I am also a practicing attorney and advisor to companies operating high-risk, high-consequence activities. I have raised money from NSF, from many companies, and I led a grant-making foundation.
My governance philosophy is guided by several high-level principles and concerns: our institution’s competitive posture; a structural perspective on campus challenges (I believe it is important to avoid using policies that impose costs on individuals when the problem being addressed is systemic in nature); the need to protect faculty time and attention from growing compliance, training, and other administrative obligations; and my sense that as an institution, we are becoming too risk adverse.
As a dual appointee in two professional schools (Law & Information), I have worked with many colleagues in the humanities and sciences. One of my goals has been to increase lateral faculty information sharing, and to that end I have helped moderate the Faculty Budget Forum. As a member of DIVCO, I would endeavor to help others understand and contribute to the complex governance landscape of our wonderful campus.
What conflicts of interest do you have?
The University of California recognizes that engagements in the private sector enrich academics’ research and teaching. I teach at professional schools, which tend to encourage teaching and research related to practice challenges. There’s a tradeoff between private sector engagements and benefits to students. For instance, several of my classes are based on client scenarios and my writing is informed by real business needs and constraints.
Norms surrounding conflicts disclosure and regulation is highly disciplinary. In some fields, experts think themselves above conflicts and do not disclose them. In others, such as law, norms of client confidentiality cause some academics to keep their conflicts secret. And some universities allow study sponsors to control the outcomes of research—something that is explicitly prohibited at Cal.
I serve on boards to two companies, Constella Intelligence (cybersecurity intelligence) and Palantir Technologies. I have also served on the boards of non-profits and operated a foundation, but no one seems concerned about those conflicts, and if you ask me in person, I’ll explain why you should be 🙂 Since 2015, I have been of counsel to Gunderson Dettmer LLP, where I advised scores of emerging technology companies and venture clients. The identities of my Gunderson clients are confidential, but I don’t engage in any kind of legal/expert opinion writing, public advocacy, or research for these clients. Instead, I typically help them with discrete legal problems.
My work has been directly or indirectly supported by many technology companies, including Apple, Google, Microsoft, Palantir, and Nokia. I always disclose specific sponsors of my research projects, and all situations where my academic work may be colored by a client or sponsor.
What is the Privacy Law Scholars Conference (PLSC)?
With Dan Solove, I started the Privacy Law Scholars Conference in 2008 (PLSC). The PLSC is a paper workshop for in-progress scholarship related to information privacy. The conference was based on the well-established Intellectual Property Law Scholars Conference and some ideas we borrowed from other conference: long networking breaks, all conversations, an emphasis on collegial and helpful interactions, and no panels. We also adopted the practice of having papers presented by a “commenter”—a designated discussion leader who introduced the paper and then curated the conversation amongst the group. This last innovation is key. It creates a lively dynamic where you don’t have the author droning on and on. It also helps the author understand what the reader actually learned from the paper. Many of the most important articles in the privacy law field were workshopped at PLSC.
I am no longer involved in PLSC, but am proud of what it has become, and am delighted that the model has been deployed elsewhere. There are now PLSCs in Europe, Latin America, and even regional mini-PLSCs in the US.
I am an undergrad/grad, may I take your course?
Probably yes.
Graduate students, you can enroll if my course has a non-Law prefix, such as Info.
Undergraduate students, you can enroll in INFO and Legal Studies (but not LAW) courses with permission. To obtain permission, email me the following information. I typically enroll undergraduates after the graduate registration period.
1. I am an upper-division student [Yes/No]
2. What year?
3. I understand and accept that this is a graduate-level class, with graduate-level materials and pacing. [Yes/No]
4. I understand and accept that participation in class discussion is expected, even if the class is larger than most undergraduate courses that expect this (in grad and law school classes, for example, students participate in discussion in 50-100-person classes). [Yes/No]
5. I would like to take this class because: [Please tell us why you would like to take the class.]
6. I would contribute to this class because: [Please tell us why you would contribute to the class. For example, your major is relevant to topics in the class; you are doing an undergrad thesis on a relevant topic; you worked on relevant issues prior to coming to Berkeley; etc.]
Will you write me a letter of recommendation?
Probably yes 🙂 But I need a few things from you in order to do a great job.
First, faculty need time. A month before the deadline is great.
Second, could you send me the following information:
- The position title and submission information.
- Information about the position
- Your resume or CV
- A short description of your long-term career goals
- In your own words, why you think you are a good fit for the opportunity
- In your own words, why you think the opportunity is a good one
Where can I find your LaTeX templates?
Check out my Github for:
Old school Berkeley letterhead
The 2020 Berkeley formal letterhead
The 2020 Berkeley casual letterhead
What is your AI-compliant email auto-responder message?
Pursuant to Article 52 of the EU AI Act, please be aware that this message comes from a low-risk \”AI\” system and not a human. All AI systems pose risks, including but not limited to spreading misinformation, causing emotional manipulation, engaging in invidious discrimination, the mis-operation of lethal autonomous weapons systems, the erosion of all human responsibility for decision-making and good judgment, the rendering useless of humanity, and/or a mass extinction event from misaligned superintelligence. Any information produced by this system must be processed with the highest caution. The University of California disclaims any claims or disclaimers made by this system. Do not rely on any information conveyed here without verifying it. You have no rights under Article 22 of the GDPR to object to this system, because sending email to this address is explicit consent to automated processing, including profiling. This system is not pre-registered in China; emails received from this system in China are hereby recalled.