Chris Jay Hoofnagle is Professor of Law in Residence at the University of California, Berkeley, School of Law, where he teaches cybersecurity, programming for lawyers, and torts. He is affiliated faculty with the Simons Institute for the Theory of Computing and the Center for Security in Politics. In Spring 2024, Hoofnagle visitied King’s College Department of War Studies.
Hoofnagle’s new book with Golden G. Richard III is Cybersecurity in Context (Wiley forthcoming 2024). Previous works include Law and Policy for the Quantum Age (with Simson Garfinkel, 2022) and Federal Trade Commission Privacy Law and Policy (2016), both with Cambridge University Press.
An elected member of the American Law Institute, Hoofnagle is of counsel to Gunderson Dettmer LLP, a longtime advisor to Palantir Technologies, and a member of the National Academies Intelligence Science and Technology Experts Group (ISTEG).
With Professor Daniel Solove, Hoofnagle founded the Privacy Law Scholars Conference.

In-progress works
-
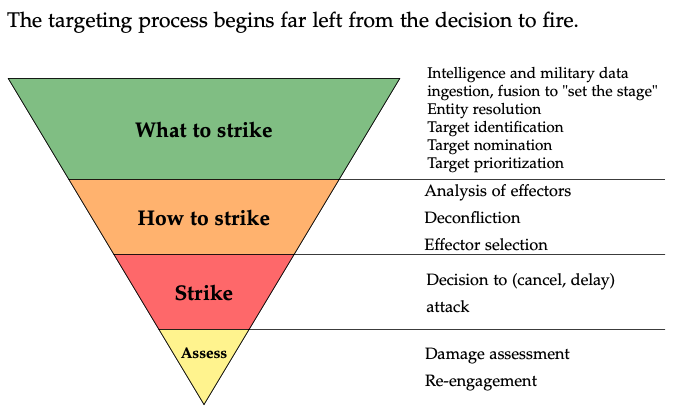
Military ML: Missing the Target
Are we on the precipice of developing autonomous killer robots; unmanned technologies that will completely dominate conflict, remorselessly, perfectly? Some advocates think so but this article explains why the killer robot view is misplaced and in its misdirection, draws attention away from how militaries are likely to use machine learning (ML) and artificial intelligence (AI)…
-
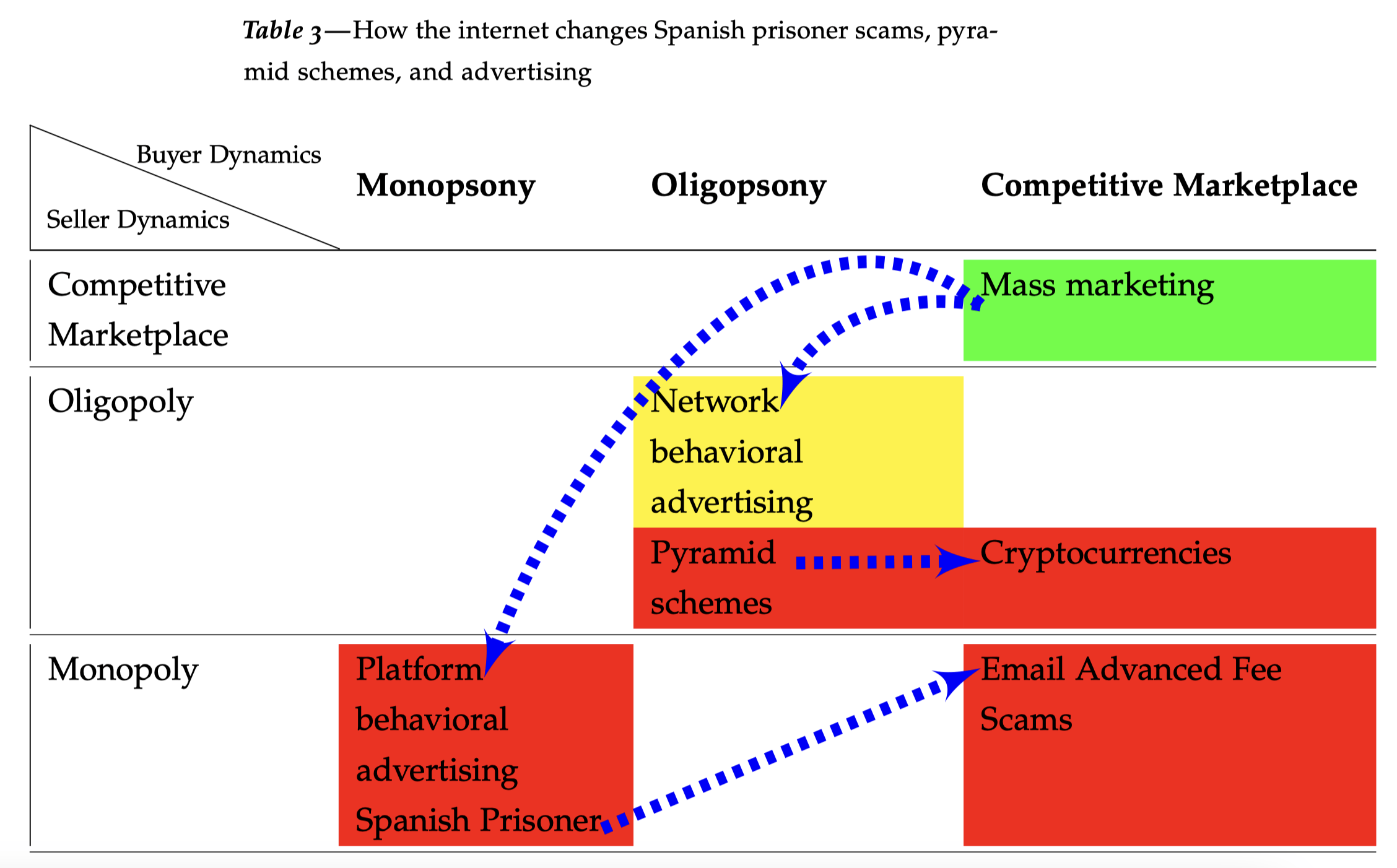
The Techcons
Revisiting Arthur Leff’s Swindling and Selling Yale Law Professor Arthur Leff wrote a powerful, market-structure analysis of consumer fraud in his 1976 Swindling and Selling. That work is more or less lost to history. Leff explained that con artists attempted to impose a false economy on marks. In a perfect congame, such as the Spanish Prisoner,…
-
What is consumer privacy?
In this essay for a lecture at Stanford University, I attempt to explain consumer privacy as a deterrence theory strategy. I argue that privacy does have methods of analysis, based in fair information practices, while popular use of the term “privacy” is loose, a shibboleth representing uncertain values. This wide-ranging essay then goes on to…
Publications
h-index: 32, i10: 43

Hoofnagle, Chris Jay; Kesari, Aniket; Perzanowski, Aaron
The Tethered Economy Journal Article
In: Geo. Wash. L. Rev., vol. 87, no. 4, pp. 783, 2019.
Abstract | Links | BibTeX | Tags: Antitrust Law, Competition Law, Consumer Protection
@article{hoofnagle2019tethered,
title = {The Tethered Economy},
author = {Chris Jay Hoofnagle and Aniket Kesari and Aaron Perzanowski},
url = {https://www.gwlr.org/the-tethered-economy/
https://www.gwlr.org/wp-content/uploads/2019/10/87-Geo.-Wash.-L.-Rev.-783.pdf},
year = {2019},
date = {2019-01-01},
journal = {Geo. Wash. L. Rev.},
volume = {87},
number = {4},
pages = {783},
abstract = {Imagine a future in which every purchase decision is as complex as choosing a mobile phone. What will ongoing service cost? Is it compatible with other devices you use? Can you move data and applications across devices? Can you switch providers? These are just some of the questions one must consider when a product is “tethered” or persistently linked to the seller. The Internet of Things, but more broadly, consumer products with embedded software, are already tethered.
While tethered products bring the benefits of connection, they also carry its pathologies. As sellers blend hardware and software—as well as product and service—tethers yoke the consumer to a continuous post-transaction relationship with the seller. The consequences of that dynamic will be felt both at the level of individual consumer harms and on the scale of broader, economy-wide effects. These consumer and market-level harms, while distinct, reinforce and amplify one another in troubling ways.
Seller contracts have long sought to shape consumers’ legal rights. But in a tethered environment, these rights may become nonexistent as legal processes are replaced with automated technological enforcement. In such an environment, the consumer-seller relationship becomes extractive, more akin to consumers captive in an amusement park than to a competitive marketplace in which many sellers strive to offer the best product for the lowest price.
At the highest level, consumer protection law is concerned with promoting functioning free markets and insulating consumers from harms stemming from information asymmetries. We conclude by exploring legal options to reduce the pathologies of the tethered economy.},
keywords = {Antitrust Law, Competition Law, Consumer Protection},
pubstate = {published},
tppubtype = {article}
}
While tethered products bring the benefits of connection, they also carry its pathologies. As sellers blend hardware and software—as well as product and service—tethers yoke the consumer to a continuous post-transaction relationship with the seller. The consequences of that dynamic will be felt both at the level of individual consumer harms and on the scale of broader, economy-wide effects. These consumer and market-level harms, while distinct, reinforce and amplify one another in troubling ways.
Seller contracts have long sought to shape consumers’ legal rights. But in a tethered environment, these rights may become nonexistent as legal processes are replaced with automated technological enforcement. In such an environment, the consumer-seller relationship becomes extractive, more akin to consumers captive in an amusement park than to a competitive marketplace in which many sellers strive to offer the best product for the lowest price.
At the highest level, consumer protection law is concerned with promoting functioning free markets and insulating consumers from harms stemming from information asymmetries. We conclude by exploring legal options to reduce the pathologies of the tethered economy.

Boerman, Sophie C; Helberger, Natali; Noort, Guda; Hoofnagle, Chris Jay
Sponsored Blog Content: What Do the Regulations Say: And What Do Bloggers Say Journal Article
In: J. Intell. Prop. Info. Tech. & Elec. Com. L., vol. 9, pp. 146, 2018.
Abstract | Links | BibTeX | Tags: Consumer Protection
@article{boerman2018sponsored,
title = {Sponsored Blog Content: What Do the Regulations Say: And What Do Bloggers Say},
author = {Sophie C Boerman and Natali Helberger and Guda Noort and Chris Jay Hoofnagle},
url = {https://www.jipitec.eu/archive/issues/jipitec-9-2-2018/4730/JIPITEC_9_2_2018_146_Boerman_et_al},
year = {2018},
date = {2018-01-01},
journal = {J. Intell. Prop. Info. Tech. & Elec. Com. L.},
volume = {9},
pages = {146},
abstract = {Influencer marketing – the use of opinion leaders such as bloggers with many followers and readers to disseminate product messages – is gaining advertisers’ interest. This paper presents the law and self-regulative provisions concerning blog advertising in both Europe and the US and documents the actual practice of disclosing blog advertising: whether and if so how, bloggers disclose influences from advertisers, and how these disclosures align with the regulations in place. The Federal Trade Commission Act and related guides in the US, and self-regulative provisions in Europe urge advertisers and endorsers, such as bloggers, to disclose any commercial relationship. These disclosures should be clear and conspicuous because advertising to consumers should be recognizable as such. Although advertisers increasingly encourage bloggers to promote products, it is unclear whether bloggers comply with disclosure requirements.
To test compliance with disclosure requirements, we performed a content analysis of 200 blog posts drawn from the top-20-ranked sites in the Netherlands and the United States. We found that 65% of the posts mention brands and products. Yet, only 15% of the blog posts provided some commercial sponsorship disclosure. To determine whether posts mentioning brands were organic, unsponsored endorsements, we made repeated attempts to contact authors. Of those that responded, most claimed that their writing was not sponsored, but a small number received remuneration and did not disclose it. Furthermore, among the disclosing bloggers, we found regular problems in their sponsorship disclosures: many only state ‘sponsored’ or ‘affiliated link’; only 1/3 stated the name of the actual sponsor; most require the users to “scroll down,”; and most are in the same font as ordinary text. Our findings raise several regulatory issues; namely, the need for more concrete guidance on disclosure format, and it highlights the difficulty of monitoring compliance with the existing provisions. In so doing, our findings also provide important input for the European Commission’s Regulatory Fitness and Performance exercise, which tackles, among others the Unfair Commercial Practice Directive.},
keywords = {Consumer Protection},
pubstate = {published},
tppubtype = {article}
}
To test compliance with disclosure requirements, we performed a content analysis of 200 blog posts drawn from the top-20-ranked sites in the Netherlands and the United States. We found that 65% of the posts mention brands and products. Yet, only 15% of the blog posts provided some commercial sponsorship disclosure. To determine whether posts mentioning brands were organic, unsponsored endorsements, we made repeated attempts to contact authors. Of those that responded, most claimed that their writing was not sponsored, but a small number received remuneration and did not disclose it. Furthermore, among the disclosing bloggers, we found regular problems in their sponsorship disclosures: many only state ‘sponsored’ or ‘affiliated link’; only 1/3 stated the name of the actual sponsor; most require the users to “scroll down,”; and most are in the same font as ordinary text. Our findings raise several regulatory issues; namely, the need for more concrete guidance on disclosure format, and it highlights the difficulty of monitoring compliance with the existing provisions. In so doing, our findings also provide important input for the European Commission’s Regulatory Fitness and Performance exercise, which tackles, among others the Unfair Commercial Practice Directive.

Perzanowski, Aaron; Hoofnagle, Chris Jay
What We Buy When We ‘Buy Now’ Journal Article
In: University of Pennsylvania Law Review, vol. 165, pp. 315, 2017.
Abstract | Links | BibTeX | Tags: Consumer Protection
@article{perzanowski2016we,
title = {What We Buy When We 'Buy Now'},
author = {Aaron Perzanowski and Chris Jay Hoofnagle},
url = {https://scholarship.law.upenn.edu/cgi/viewcontent.cgi?article=9564&context=penn_law_review},
year = {2017},
date = {2017-01-01},
journal = {University of Pennsylvania Law Review},
volume = {165},
pages = {315},
abstract = {This Article presents the results of the first study of the impact of marketing language like the Buy Now button on the beliefs and behavior of digital media consumers. Our data demonstrate that a sizable percentage of consumers is misled with respect to the rights they acquire when they “buy” digital media goods. They mistakenly believe they can keep those goods permanently, lend them to friends and family, give them as gifts, leave them in their wills, resell them, and use them on their devices of choice.},
keywords = {Consumer Protection},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay
FTC Regulation of Cybersecurity and Surveillance Book Section
In: Gray, David; Henderson, Stephen (Ed.): The Cambridge Handbook of Surveillance Law, Cambridge Univ. Press, 2017.
Abstract | Links | BibTeX | Tags: Consumer Protection, FTC, Privacy
@incollection{hoofnagle2017ftc,
title = {FTC Regulation of Cybersecurity and Surveillance},
author = {Chris Jay Hoofnagle},
editor = {David Gray and Stephen Henderson},
url = {https://www.cambridge.org/core/books/abs/cambridge-handbook-of-surveillance-law/ftc-regulation-of-cybersecurity-and-surveillance/BE91AB5F9B59B3923B7D93CBD6834C6A},
year = {2017},
date = {2017-01-01},
booktitle = {The Cambridge Handbook of Surveillance Law},
publisher = {Cambridge Univ. Press},
abstract = {The Federal Trade Commission (FTC) is the United States’ chief consumer protection agency. Through its mandate to prevent unfair and deceptive trade practices, it both regulates surveillance and creates cybersecurity law. This chapter details how the FTC regulates private-sector surveillance and elucidates several emergent properties of the agency’s activities. First, private-sector surveillance shapes individuals’ reasonable expectations of privacy, and thus regulation of the private-sector has effects on the government as surveillant. The FTC’s activities not only serve dignity interests in preventing commercial inference in one’s life, they also affect citizens’ civil liberties posture with the state. Second, surveillance can make companies directly liable (for intrusive web monitoring, for tracking people off-line, and for installing malware) or indirectly liable (for creating insecure systems, for using deception to investigate, and for mediating the surveillance of others) under the FTC Act. Third, the FTC’s actions substitute for private actions, because the class action is burdened in novel ways. Fourth, the FTC’s actions increase the quality of consent necessary to engage in surveillance, and in so doing, the FTC has made some kinds of surveillance practically impossible to implement legally. Finally, the FTC’s actions make companies more responsible for their surveillance technologies in several ways – by making software vendors liable for users’ activities, by imposing substantive security duties, and by narrowing Internet intermediary immunity.},
keywords = {Consumer Protection, FTC, Privacy},
pubstate = {published},
tppubtype = {incollection}
}
Eijk, Nico; Hoofnagle, Chris Jay; Kannekens, Emilie
Unfair Commercial Practices: A Complementary Approach to Privacy Protection Journal Article
In: Eur. Data Prot. L. Rev., vol. 3, pp. 325, 2017.
Abstract | Links | BibTeX | Tags: Consumer Protection, Privacy
@article{van2017unfair,
title = {Unfair Commercial Practices: A Complementary Approach to Privacy Protection},
author = {Nico Eijk and Chris Jay Hoofnagle and Emilie Kannekens},
url = {https://heinonline.org/HOL/LandingPage?handle=hein.journals/edpl3&div=61&id=&page=},
year = {2017},
date = {2017-01-01},
journal = {Eur. Data Prot. L. Rev.},
volume = {3},
pages = {325},
abstract = {Millions of European internet users access online platforms where their personal data is being collected, processed, analysed or sold. The existence of some of the largest online platforms is entirely based on data driven business models. In the European Union, the protection of personal data is considered a fundamental right. Under Article 8(3) of the EU Charter of Fundamental Rights, compliance with data protection rules should be subject to control by an independent authority. In the EU, enforcement of privacy rules almost solely takes place by the national data protection authorities. They typically apply sector-specific rules, based on the EU Data Protection Directive. In the United States, the Federal Trade Commission is the primary enforcer of consumers’ (online) privacy interests. The agency’s competence is not based on the protection of fundamental rights, but on the basis that maintenance of a competitive, fair marketplace will provide the right choices for consumers to take. In this Article the US legal framework will be discussed and compared to the EU legal framework, which forms our finding that in the EU rules on unfair commercial practices could be enforced in a similar manner to protect people’s privacy. In the EU, the many frictions concerning the market/consumer-oriented use of personal data form a good reason to actually deal with these frictions in a market/consumer legal framework.},
keywords = {Consumer Protection, Privacy},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay
Federal Trade Commission Privacy Law and Policy Book
Cambridge University Press, 2016.
Abstract | Links | BibTeX | Tags: Consumer Protection, FTC, Privacy, Public Choice Theory
@book{hoofnagle2016federal,
title = {Federal Trade Commission Privacy Law and Policy},
author = {Chris Jay Hoofnagle},
url = {https://www.cambridge.org/core/books/federal-trade-commission-privacy-law-and-policy/},
year = {2016},
date = {2016-01-01},
publisher = {Cambridge University Press},
abstract = {The Federal Trade Commission, a US agency created in 1914 to police the problem of 'bigness', has evolved into the most important regulator of information privacy - and thus innovation policy - in the world. Its policies profoundly affect business practices and serve to regulate most of the consumer economy. In short, it now regulates our technological future. Despite its stature, however, the agency is often poorly understood by observers and even those who practice before it. This volume by Chris Jay Hoofnagle - an internationally recognized scholar with more than fifteen years of experience interacting with the FTC - is designed to redress this confusion by explaining how the FTC arrived at its current position of power. It will be essential reading for lawyers, legal academics, political scientists, historians and anyone else interested in understanding the FTC's privacy activities and how they fit in the context of the agency's broader consumer protection mission.},
keywords = {Consumer Protection, FTC, Privacy, Public Choice Theory},
pubstate = {published},
tppubtype = {book}
}
Hoofnagle, Chris Jay
Assessing the Federal Trade Commission’s Privacy Assessments Journal Article
In: IEEE Security & Privacy, vol. 14, no. 2, pp. 58–64, 2016.
Abstract | Links | BibTeX | Tags: Consumer Protection, FTC
@article{hoofnagle2016assessing,
title = {Assessing the Federal Trade Commission's Privacy Assessments},
author = {Chris Jay Hoofnagle},
url = {https://www.computer.org/csdl/magazine/sp/2016/02/msp2016020058/13rRUxcbnAR},
year = {2016},
date = {2016-01-01},
journal = {IEEE Security & Privacy},
volume = {14},
number = {2},
pages = {58–64},
publisher = {IEEE},
abstract = {Regulators worldwide need to keep tabs on companies caught violating consumer protection rules. Assessments by outside accounting firms are a key tool for regulators to detect privacy and security problems. It's not widely known that an assessment, a term of art in accounting, is a less-intense evaluation than an audit. Also, in practice, assessments overseen by America's top consumer protection cop, the US Federal Trade Commission, fall short of what's needed to ensure that information-intensive companies are protecting privacy and honoring promises. This article outlines five practical steps to make company oversight more effective.},
keywords = {Consumer Protection, FTC},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay
US Regulatory Values and Privacy Consequences Journal Article
In: Eur. Data Prot. L. Rev., vol. 2, pp. 169, 2016.
Abstract | Links | BibTeX | Tags: Consumer Protection, GDPR, Privacy
@article{hoofnagle2016us,
title = {US Regulatory Values and Privacy Consequences},
author = {Chris Jay Hoofnagle},
url = {https://edpl.lexxion.eu/article/edpl/2016/2/7},
year = {2016},
date = {2016-01-01},
journal = {Eur. Data Prot. L. Rev.},
volume = {2},
pages = {169},
abstract = {Europeans have long faced a regulatory challenge: how can the human rights and dignitary values that animate data protection law be protected in transborder data flows?},
keywords = {Consumer Protection, GDPR, Privacy},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay
FTC’s Early Consumer Protection Challenges Endure Journal Article
In: Law360, 2016.
Abstract | Links | BibTeX | Tags: Consumer Protection, FTC, Privacy
@article{hoofnagle2016challenges,
title = {FTC's Early Consumer Protection Challenges Endure},
author = {Chris Jay Hoofnagle},
url = {https://www.law360.com/articles/753384/ftc-s-early-consumer-protection-challenges-endure},
year = {2016},
date = {2016-01-01},
journal = {Law360},
abstract = {The 1914 creation of the Federal Trade Commission was a radical step to address tensions in the economy. Not only was it one of the first regulatory agencies in America, the FTC was also granted nearly comprehensive jurisdiction and a broad, undefined mandate to police competition. To understand the FTC, we have to situate ourselves in the tensions of turn-of-the-century American economy. The country was rapidly changing from an agricultural to an industrial economy. A growing disconnection between creators and buyer of products created new consumer protection problems. Industries with high barriers to entry and industries that enjoyed network effects could manipulate prices and bend others to their will. The individual could sense a threat to their livelihood and social condition, but not understand the broader implications of industrialization.},
keywords = {Consumer Protection, FTC, Privacy},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris; Meleshinsky, Eduard
Native Advertising and Endorsement: Schema, Source-Based Misleadingness, and Omission of Material Facts Journal Article
In: Technology Science, vol. 20151215, no. 03, 2015.
Abstract | Links | BibTeX | Tags: Advertising, Advertorials, Consumer Protection
@article{hoofnagle2015native,
title = {Native Advertising and Endorsement: Schema, Source-Based Misleadingness, and Omission of Material Facts},
author = {Chris Hoofnagle and Eduard Meleshinsky},
url = {https://techscience.org/a/2015121503/},
year = {2015},
date = {2015-01-01},
journal = {Technology Science},
volume = {20151215},
number = {03},
abstract = {Native advertising is the new term for “advertorials,” advertisements disguised as editorial content. Modern native advertising started in the 1950s, but its first uses were clearly signaled to the consumer. This paper explains why consumers might be misled by advertorials—even when labeled as such—when advertising material has elements of editorial content.},
keywords = {Advertising, Advertorials, Consumer Protection},
pubstate = {published},
tppubtype = {article}
}
Cohen, Julie E; Hoofnagle, Chris Jay; McGeveran, William; Ohm, Paul; Reidenberg, Joel R; Richards, Neil M; Thaw, David; Willis, Lauren E
Information Privacy Law Scholars’ Brief in Spokeo, Inc. v. Robins Journal Article
In: UC Berkeley Public Law Research Paper, no. 2656482, 2015.
Abstract | BibTeX | Tags: Consumer Protection, FCRA
@article{cohen2015information,
title = {Information Privacy Law Scholars' Brief in Spokeo, Inc. v. Robins},
author = {Julie E Cohen and Chris Jay Hoofnagle and William McGeveran and Paul Ohm and Joel R Reidenberg and Neil M Richards and David Thaw and Lauren E Willis},
year = {2015},
date = {2015-01-01},
journal = {UC Berkeley Public Law Research Paper},
number = {2656482},
abstract = {This brief, submitted to the Supreme Court of the United States by 15 information privacy law scholars in the case of Spokeo, Inc. v. Robins (No 13-1339), argues that in enacting the Fair Credit Reporting Act (FCRA), Congress crafted a bargain between aggressive, secretive data-aggregating businesses and the public: if those businesses limited disclosures and made reasonable efforts to adhere to practices ensuring “maximum possible accuracy,” they would enjoy a safe harbor from litigation under many other state and federal theories. The FCRA’s consumer transparency requirements and remedial provisions were designed to encourage steady improvement in consumer reporting practices and to relieve pressure on public enforcement authorities. The Petitioner’s claim that Respondents cannot pursue it for its violations of the FCRA would unravel that bargain, preserving consumer reporting agencies’ broad immunity from suit while diminishing incentives to handle data fairly.},
keywords = {Consumer Protection, FCRA},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay; Urban, Jennifer; Li, Su
Mobile Payments: Consumer Benefits & New Privacy Concerns Journal Article
In: The European Financial Review, 2013.
Abstract | Links | BibTeX | Tags: Consumer Protection, Privacy
@article{hoofnagle2013mobilepayments,
title = {Mobile Payments: Consumer Benefits & New Privacy Concerns},
author = {Chris Jay Hoofnagle and Jennifer Urban and Su Li},
url = {https://www.europeanfinancialreview.com/mobile-payments-consumer-benefits-new-privacy-concerns/},
year = {2013},
date = {2013-01-01},
journal = {The European Financial Review},
abstract = {Payment systems that allow people to transfer value using their mobile phones are promised to reduce transaction fees, increase convenience, and enhance payment security. New mobile payment systems also are likely to make it easier for businesses to identify consumers, to collect contact information on them, and to share more information about consumers’ purchases among more businesses. While many studies have reported security concerns as a barrier to the adoption of mobile payment technologies, the privacy implications of these technologies have been under examined. It is also unclear whether consumers understand the reality of greater information collection in mobile transactions over existing credit and debit alternatives.
In this article, we report on a survey study we recently completed, which seeks to better understand Americans’ attitudes towards privacy in these new transaction systems. The study focuses upon the ways that mobile payment systems are likely to share information about consumers’ purchases.},
keywords = {Consumer Protection, Privacy},
pubstate = {published},
tppubtype = {article}
}
In this article, we report on a survey study we recently completed, which seeks to better understand Americans’ attitudes towards privacy in these new transaction systems. The study focuses upon the ways that mobile payment systems are likely to share information about consumers’ purchases.
Hoofnagle, Chris Jay
Towards a Market for Bank Safety Journal Article
In: Loy. Consumer L. Rev., vol. 21, pp. 155, 2008.
Abstract | Links | BibTeX | Tags: Consumer Protection, Identity Theft
@article{hoofnagle2008towards,
title = {Towards a Market for Bank Safety},
author = {Chris Jay Hoofnagle},
url = {https://lawecommons.luc.edu/cgi/viewcontent.cgi?article=1105&context=lclr},
year = {2008},
date = {2008-01-01},
journal = {Loy. Consumer L. Rev.},
volume = {21},
pages = {155},
publisher = {HeinOnline},
abstract = {This article concludes that the available data, while weakened by several methodological concerns, do show that certain banks, large and small, have different identity theft footprints. Other discoveries were made as well. First, if present trends continue, there will be a substantial upswing in identity theft complaints to the Federal Trade Commission in 2008. Second, over a three-year period, a small group of companies accounted for almost 5o percent of identity theft incidents. Focusing interventions on this small group of companies could have a profound effect on incidence of identity theft. Finally, non-banking institutions, such as telecommunications companies, have an enormous identity theft footprint; in our highly dependent credit markets, impostors may be using these companies as stepping stones for attacks against banks.},
keywords = {Consumer Protection, Identity Theft},
pubstate = {published},
tppubtype = {article}
}
Hoofnagle, Chris Jay
Identity theft: Making the known unknowns known Journal Article
In: Harv. JL & Tech., vol. 21, pp. 97, 2007.
Abstract | Links | BibTeX | Tags: Consumer Protection, Identity Theft
@article{hoofnagle2007identity,
title = {Identity theft: Making the known unknowns known},
author = {Chris Jay Hoofnagle},
url = {https://jolt.law.harvard.edu/articles/pdf/v21/21HarvJLTech097.pdf},
year = {2007},
date = {2007-01-01},
journal = {Harv. JL & Tech.},
volume = {21},
pages = {97},
abstract = {The contours of the identity theft problem, however, are known unknowns: no one knows the prevalence of identity theft, the relative rates of “new account fraud” and “account takeover,” or the effect this crime has on the economy. What is more, the advent of “synthetic” identity theft has exacerbated these measurement difficulties.},
keywords = {Consumer Protection, Identity Theft},
pubstate = {published},
tppubtype = {article}
}
For a list of research organized by research theme/question, click here.
Teaching
-
Cybersecurity in Context
New course: Fall 2024! In fall 2024, I will teach Cybersecurity in Context in the Legal Studies program (LS 190). The course will be based on my new textbook with Golden G. Richard III. Course Description Cybersecurity has become instrumental to economic activity and human rights alike. But as digital technologies penetrate almost every aspect…
-
Cybersecurity Courses @ Cal
A growing number of faculty are offering cybersecurity courses at Cal. Consider taking: The Center for Security in Politics offers a graduate certificate in security policy. Many of the electives are open to undergraduates. They include GSPP PP 155/255 Introduction to Security Policy (Professors Janet Napolitano and Daniel Sargent) PPC285 and NUCENG 285C Nuclear Security: The…
-
Computer Programming for Lawyers

Most recent syllabus: Spring 2023. Clients increasingly want their lawyers to understand their products and services on a technical level. Regulators need to understand how their rules will be implemented in code. Lawyers increasingly need tools to automate the process of collecting, organizing, and making sense of impossibly large troves of information. Computer Programming for…
-
Torts (1L)
Welcome to your first year of law school and to torts, a topic as rich as it is traditional in legal education. Torts provides an expansive lens to learn about the American legal system. This course will cover the basics of torts and in the process, the fundamental reasons and principles underlying doctrine. Learning Goals:…
-
Cybersecurity Working Group
We will discuss cybersecurity policy among a group of graduate, professional, and undergraduate students. The FCWG will be led by Andrew Reddie in Fall 2023 and Spring 2024. Chris Hoofnagle will lead it in Spring 2025 Previous syllabi (Fall 2023, Spring 2023, Fall 2022, Fall 2021, Spring 2021, Spring 2020, Spring 2019, Spring 2018, Fall 2017, Spring 2017)
-
Technology for Lawyers Workshop (TLW)

Technology for Lawyers Workshop (TLW) is a self-paced, two-session workshop covering the computer skills most important to success in law school. By working along and doing the exercises, you’ll become a more efficient user of your computer, and in the process, develop Microsoft Word templates you can use for law school assignments. Anyone in the…
-
Inactive Courses
Privacy Law for Technologists Information privacy law profoundly shapes how internet-enabled services may work. Privacy Law for Technologists will translate the regulatory demands flowing from the growing field of privacy, information security, and consumer law to those who are creating interesting and transformative internet-enabled services. The course will meet twice a week, with the first…
Governance
Berkeley has big problems with governance. I have a hypothesis of what has gone wrong and what to do about it.
-
What is the Faculty Bearometer
The Faculty Bearometer is a one-question survey posed to the Senate Faculty on issues of teaching and governance. Read more about it here.
-
What is the Faculty Budget Forum (FBF)?
The Faculty Budget Forum is Berkeley largest email list for faculty-to-faculty interaction on governance matters.
-
Fundamental Challenge: Strategy
Understanding our terminal goals is the core challenge of governance. Our terminal goals are to have world-class research and excellent teaching. Our governance activities should focus on promoting these strategic goals, and limiting the effects of other goals on these strategic goals. It’s easier for me to get reimbursed by stodgy European universities, where I…
-
Proposed Principles for Policy Evaluation
All senate committees should consider this framework for policy analysis.
-
Questions for the Vice Chancellor for Administration
In my opinion, some of Berkeley’s biggest problems emerge from the VCA’s portfolio.
-
On Administrative Misalignment
This is my diagnosis of Berkeley’s ills: a problem I call administrative misalignment. Some administrators are not working for Berkeley; they are working for something else. Maybe themselves.
-
Comments on “Sustainability”
Comments on the Proposed Presidential Policy on Sustainable Practices Thank you for inviting comment on the Proposed Presidential Policy on Sustainable Practices (“Policy”). While well-intended, the Policy creates numerous requirements untethered from our terminal goals of excellence in research and teaching. The Policy will require effort from many staff and consultants while not improving teaching…
FAQs
What is TLW—the Technology for Lawyers Workshop?
Technology for Lawyers Workshop (TLW) is a self-paced, two-session workshop covering the computer skills most important to success in law school.
By working along and doing the exercises, you’ll become a more efficient user of your computer, and in the process, develop templates you can use for law school assignments.
Session 1 is 40 minutes long, and it focuses on your computer generally and clever uses of the Web.
Session 2 is a deep dive into Microsoft Word. In this session, you will learn how to make proper templates for your legal writing. The session is 90 minutes long.
You can self-enroll here: https://bcourses.berkeley.edu/enroll/YCXH8X
Will you serve on my quals or PhD committee?
Maybe! I am a senate member and member of both the law and information faculties, so I can serve as an outside member in many configurations. Please email me a description of your research agenda, and how you think my participation will benefit your research.
I will not pay attention to a QE or other proceeding on Zoom. Sorry.
I’ve heard about your plantar fasciitis tricks…
Yes, plantar fasciitis is super annoying. Years ago, I found a literature review (can’t find it anymore) that suggested that all interventions for plantar fasciitis were equally inefficacious, and it is a condition that takes about 18 months to heal. Ouch! Furthermore, my foot doctor told me that surgery alleviates the pain but undermines the strength of your foot.
But I discovered a few tricks:
- These boots that one wears overnight to keep your foot tensioned work quickly to alleviate acute pain. Don’t use the sock ones. Use the full size one that looks like a plastic cast for a broken foot. Don’t over tighten it. Just use it so that your foot is angled slightly more than 90 degrees. If you can’t sleep with it, the boot is probably too tight or too aggressively angled.
- Voltaren, a “arthritis pain reliever,” now available over the counter-generic as diclofenac gel, is a godsend. They key is that you can put it on your foot and avoid the digestive complications from oral anti-inflammatories. Voltaren got me running in less than a week.
- Some sports, because of how your foot is angled, do not aggravate the plantar fascia. For instance, downhill skiing is great—your foot is stretched by the ski boot, making it almost like an hours-long treatment. Similarly ice skating does not aggravate my fascia even if done for hours. So you can keep in shape.
- I’ve found that the elliptical trainer doesn’t aggravate plantar fascia, and so you can do it for hours without injury. Don’t buy a cheap elliptical, they’re junk. Don’t trust the reviews either. You need to spend over $1k. The Sole E35 is a solid choice. But my favorite elliptical is the Octane XT and Q series standing ellipticals, which have stride lengths over 20 inches. You can find them on Craig’s List. I bought one used from a commercial gym for about $1k.
- Watch out for watches! I got a new Garmin watch, and it nudged me to run long and longer. I found myself running 10ks every other day, and then ended up with plantar again, putting me back at 2 mile runs…
Don’t overdo it. When I feel pressure in my heel, I know I am close to injuring my plantar fascia. So, for me at least, this is a permanent running injury 🙁
How do you contribute to DEI at Berkeley?
Technology law as a field is not known as being particularly diverse, nor inclusive. In my career at Berkeley, I have taken specific, sustained action to promote women in higher education, to raise awareness of SES issues in technology, and to include underrepresented and minority students in my work. Come by my office hours and I can speak with you in greater detail about these efforts. I’d also love to hear your thoughts about how BCLT can address systemic inequalities.
Recent events have caused me to deepen diversity and inclusion efforts in teaching. I plan to devote more classroom time to the structural causes of exclusion and inequality. For instance, in my technology courses generally, I intend to connect students with the history of Silicon Valley, and the root causes that made the area and its most successful companies homogenous. Few people know that Lockheed was the largest employer in the Valley until the rise of the .com bubble. Lockheed and other defense industrial base companies were male and white dominant (Lockheed was 85% male and 90% white even after equal opportunity laws were enacted). The demands of secrecy surrounding the DIB, the military R&D subject matter, and other factors caused systematic exclusion since the 1940s. Thus, when we think about inclusion in tech today, we have to contemplate addressing decades of disadvantage.
Confronting inequality is also a key element in my pure doctrinal courses, such as torts. I use the Witt/Tani casebook because it starts by situating the institutions of torts, because it explains how key doctrines compensate women and minorities and the poor differently, and because many of the cases selected by Witt and Tani have clear social class or race dynamics. Traditional cases that never received a class analysis—from Vosburg to Palsgraf—are recast in their casebook. My aim is to arm students with these insights so they can critically discuss the tradeoffs and implications of legal policies that promote formal equality or substantive equity.
Where can I find Berkeley Old Style Fonts?
What is the Faculty Budget Forum (FBF)?
The Faculty Budget Forum (FBF) is an email list of about 400 Berkeley faculty members. It is among the largest lateral (department to department) lists we have—the other being Teach-Net. If you are a faculty member, I am happy to add you to FBF. Just email me.
Will you supervise my JSP or JSD (PhD in law)?
Maybe! It is a delight to have a multi-year collaboration with JSP and JSD students. But JSP and JSD degrees require serious commitment because the point is not just for you to learn, but for you to make a new contribution to the literature. When you write your purpose statement, it’s not enough to just identify a topic. You must drill down and identify:
- The intellectual ideas that you want to engage in
- The literature surrounding your proposal, and how your investigation will answer problems not yet explored adequately
- Ideas that are “big enough” to justify a multi-year exploration
- Ideas that are important enough to justify the exploration—after all, you are going to spend years of your life on it 🙂
- The reasons why Berkeley is the right place for this exploration (what faculty/departmental/institutional characteristics of Berkeley are a good match for you)
- The training/experience you have that will make you successful in the research journey
Whom have you mentored at Berkeley?
Despite teaching in a professional program, I’ve had the chance to mentor some graduate students, including:
- Shazeda Ahmed, Berkeley PhD
- Zehra Betul Ayranci, Berkeley PhD, Fox Sports
- James Carney, Joanne Jia, Archana Kulkarni, Cameron Lopez, PrivacyBot Capstone Project (Information)
- Ella Corren, JSP
- Amit Elazari Bar On, head of global cybersecurity, Intel
- Gal Forer, JSD
- Kevin Frazier, USD Law
- Alexi Pfeffer-Gillett, UMD Law
- Grace Gordon, Master of Development Practice
- Arianne Jimenez, Privacy and Public Policy Manager Facebook APAC
- Aniket Kesari, Yale/Berkeley JD/PhD, Fordham Law
- Irene Kamara, Standardising data protection: a European perspective in an interconnected world, Tilburg University (Netherlands)
- Sam Kumkar, EECS
- Morgan Livingston, ISF
- Sylvia Lu, Law
- Rachna Mandalam, ISF
- Nicole van der Meulen, EC3
- Andrew Reddie, UC Berkeley
- Nikita Samarin, EECS
- Ankeet Shankar, Capstone Project (Information)
- Bart van der Sloot, Tilburg University
- Ashkan Soltani, privacy/security researcher
- Eric Winkofsky, JSD
In addition to these students, with Dean Shankar Sastry, I was Co-PI of a program (TRUST SITE REU) with a goal to increase diversity in graduate STEM programs. We hosted scores of undergraduates at Cal, and in some cases, I published papers with these students, including Mika Ayenson (Johns Hopkins University Applied Physics Laboratory), Shannon Canty, Quentin Mayo, and Lauren Thomas.
I’m a prospective student, will you…?
Apologies, I generally do not meet with students unless they are admitted to a program. Similarly, if you are a student at another program, apologies, I cannot supervise or give you advice on your research.
Please know that admissions at Berkeley is handled by a committee and that I have no influence over decisions.
What is your role with the academic senate?
I ran for the UCB Divisional Council in 2022 and won election for the 22-23, and 23-24 years. Known as DIVCO, the body could be thought of as the executive arm of Berkeley’s academic senate. I ran because of concerns about campus priorities and the strategic challenges we face. Berkeley is facing macro constraints including costs of housing and living in the Bay Area that are steadily eroding our competitive posture, and at the same time we lack features that help institutions perform (biggest example: no medical school).
We should be thinking big, with eyes on a 2030–2040 horizon. Some of the ideas I think are worth pursuing include: creating faculty housing like that offered at NYU and Colombia, creating student housing close to campus—even using eminent domain to reform the sleepy properties that surround the campus, rethinking how much of our central campus is devoted to sports infrastructure, building a medical school, and developing campus institutions that can more competitively interact with D/I/H-ARPA.
We should fundamentally rethink how we can use campus resources to compete for and retain faculty. Other schools use campus resources to provide perks for faculty that we simply don’t consider. For instance, we have a fantastic eye clinic at Berkeley—why won’t we offer corrective vision surgery as a retention strategy, or as a privilege connected with earning tenure, or even as a recruitment tool for the best graduate students?
I also ran because in my opinion, Berkeley gets in its own way too often. We literally decide not to do “the right thing” or the strategic thing because of transaction costs we have imposed upon ourselves. We are becoming more process-based and managerial. Just as employees adopt “shadow-IT” to circumvent bad technology decisions, some faculty employ shadow-operations to get their work done.
Senior faculty members spend much of their time now on process and paperwork. We need to formally declare a time-value to faculty member time, and eliminate rules, trainings, and paperwork that 1) excessively impose upon faculty time or 2) are not risk-justified. From reimbursements to CPHS to IACUC to even the merit review process, we have no evaluative method that acts as a ceiling on paperwork and faculty time and we don’t probe the upside/downside risks from process requirements.
Candidate Statement
My governance experience at Cal includes campus-level (CPHS, leading the Center for Long Term Cybersecurity, developing a professional masters in cybersecurity, Senate academic freedom committee) and school-level service (HGA of our cyber program, building space, admissions). I am a former member of the AAUP’s Committee A on Academic Freedom and Tenure and helped it develop policy on protection of electronic communications. I am also a practicing attorney and advisor to companies operating high-risk, high-consequence activities. I have raised money from NSF, from many companies, and I led a grant-making foundation.
My governance philosophy is guided by several high-level principles and concerns: our institution’s competitive posture; a structural perspective on campus challenges (I believe it is important to avoid using policies that impose costs on individuals when the problem being addressed is systemic in nature); the need to protect faculty time and attention from growing compliance, training, and other administrative obligations; and my sense that as an institution, we are becoming too risk adverse.
As a dual appointee in two professional schools (Law & Information), I have worked with many colleagues in the humanities and sciences. One of my goals has been to increase lateral faculty information sharing, and to that end I have helped moderate the Faculty Budget Forum. As a member of DIVCO, I would endeavor to help others understand and contribute to the complex governance landscape of our wonderful campus.
What conflicts of interest do you have?
The University of California recognizes that engagements in the private sector enrich academics’ research and teaching. I teach at professional schools, which tend to encourage teaching and research related to practice challenges. There’s a tradeoff between private sector engagements and benefits to students. For instance, several of my classes are based on client scenarios and my writing is informed by real business needs and constraints.
Norms surrounding conflicts disclosure and regulation is highly disciplinary. In some fields, experts think themselves above conflicts and do not disclose them. In others, such as law, norms of client confidentiality cause some academics to keep their conflicts secret. And some universities allow study sponsors to control the outcomes of research—something that is explicitly prohibited at Cal.
I serve on boards to two companies, Constella Intelligence (cybersecurity intelligence) and Palantir Technologies. I have also served on the boards of non-profits and operated a foundation, but no one seems concerned about those conflicts, and if you ask me in person, I’ll explain why you should be 🙂 Since 2015, I have been of counsel to Gunderson Dettmer LLP, where I advised scores of emerging technology companies and venture clients. The identities of my Gunderson clients are confidential, but I don’t engage in any kind of legal/expert opinion writing, public advocacy, or research for these clients. Instead, I typically help them with discrete legal problems.
My work has been directly or indirectly supported by many technology companies, including Apple, Google, Microsoft, Palantir, and Nokia. I always disclose specific sponsors of my research projects, and all situations where my academic work may be colored by a client or sponsor.
What is the Privacy Law Scholars Conference (PLSC)?
With Dan Solove, I started the Privacy Law Scholars Conference in 2008 (PLSC). The PLSC is a paper workshop for in-progress scholarship related to information privacy. The conference was based on the well-established Intellectual Property Law Scholars Conference and some ideas we borrowed from other conference: long networking breaks, all conversations, an emphasis on collegial and helpful interactions, and no panels. We also adopted the practice of having papers presented by a “commenter”—a designated discussion leader who introduced the paper and then curated the conversation amongst the group. This last innovation is key. It creates a lively dynamic where you don’t have the author droning on and on. It also helps the author understand what the reader actually learned from the paper. Many of the most important articles in the privacy law field were workshopped at PLSC.
I am no longer involved in PLSC, but am proud of what it has become, and am delighted that the model has been deployed elsewhere. There are now PLSCs in Europe, Latin America, and even regional mini-PLSCs in the US.
I am an undergrad/grad, may I take your course?
Probably yes.
Graduate students, you can enroll if my course has a non-Law prefix, such as Info.
Undergraduate students, you can enroll in INFO and Legal Studies (but not LAW) courses with permission. To obtain permission, email me the following information. I typically enroll undergraduates after the graduate registration period.
1. I am an upper-division student [Yes/No]
2. What year?
3. I understand and accept that this is a graduate-level class, with graduate-level materials and pacing. [Yes/No]
4. I understand and accept that participation in class discussion is expected, even if the class is larger than most undergraduate courses that expect this (in grad and law school classes, for example, students participate in discussion in 50-100-person classes). [Yes/No]
5. I would like to take this class because: [Please tell us why you would like to take the class.]
6. I would contribute to this class because: [Please tell us why you would contribute to the class. For example, your major is relevant to topics in the class; you are doing an undergrad thesis on a relevant topic; you worked on relevant issues prior to coming to Berkeley; etc.]
Will you write me a letter of recommendation?
Probably yes 🙂 But I need a few things from you in order to do a great job.
First, faculty need time. A month before the deadline is great.
Second, could you send me the following information:
- The position title and submission information.
- Information about the position
- Your resume or CV
- A short description of your long-term career goals
- In your own words, why you think you are a good fit for the opportunity
- In your own words, why you think the opportunity is a good one
Where can I find your LaTeX templates?
Check out my Github for:
Old school Berkeley letterhead
The 2020 Berkeley formal letterhead
The 2020 Berkeley casual letterhead
What is your AI-compliant email auto-responder message?
Pursuant to Article 52 of the EU AI Act, please be aware that this message comes from a low-risk “AI” system and not a human. All AI systems pose risks, including but not limited to spreading misinformation, causing emotional manipulation, engaging in invidious discrimination, the mis-operation of lethal autonomous weapons systems, the erosion of all human responsibility for decision-making and good judgment, the rendering useless of humanity, and/or a mass extinction event from misaligned superintelligence. Any information produced by this system must be processed with the highest caution. The University of California disclaims any claims or disclaimers made by this system. Do not rely on any information conveyed here without verifying it. You have no rights under Article 22 of the GDPR to object to this system, because sending email to this address is explicit consent to automated processing, including profiling. This system is not pre-registered in China; emails received from this system in China are hereby recalled.