Category: Research
-

Cybersecurity in Context
Cybersecurity in Context is forthcoming from Wiley September 2024! Pre-order here. Every one now has a stake in the healthy functioning of communications and control networks, in the devices and services dependent on network, and by implication, in all the complicated infrastructure required to keep networks, devices, and services operating. As we have become more…
-
The Techcons
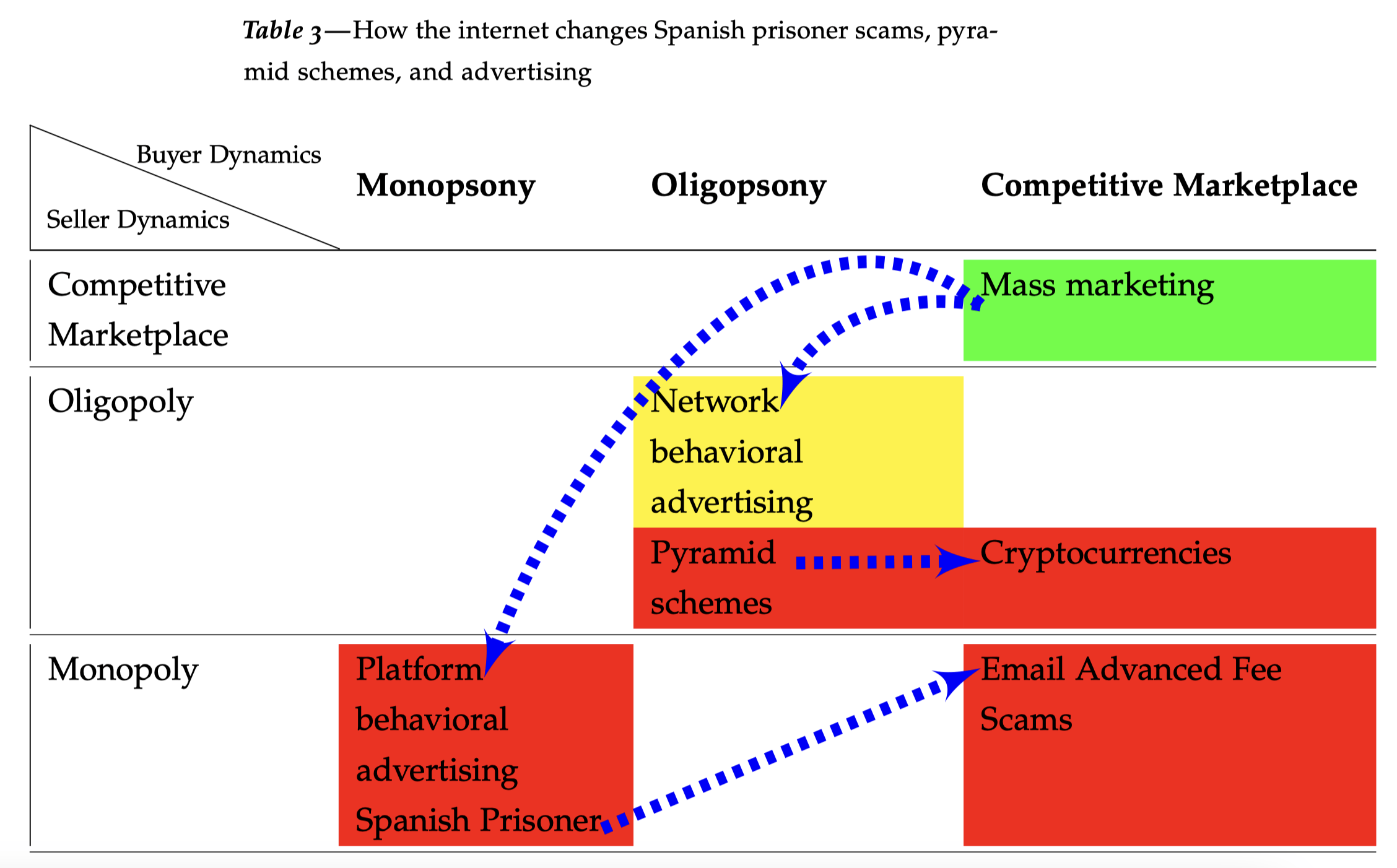
Revisiting Arthur Leff’s Swindling and Selling Yale Law Professor Arthur Leff wrote a powerful, market-structure analysis of consumer fraud in his 1976 Swindling and Selling. That work is more or less lost to history. Leff explained that con artists attempted to impose a false economy on marks. In a perfect congame, such as the Spanish Prisoner,…
-
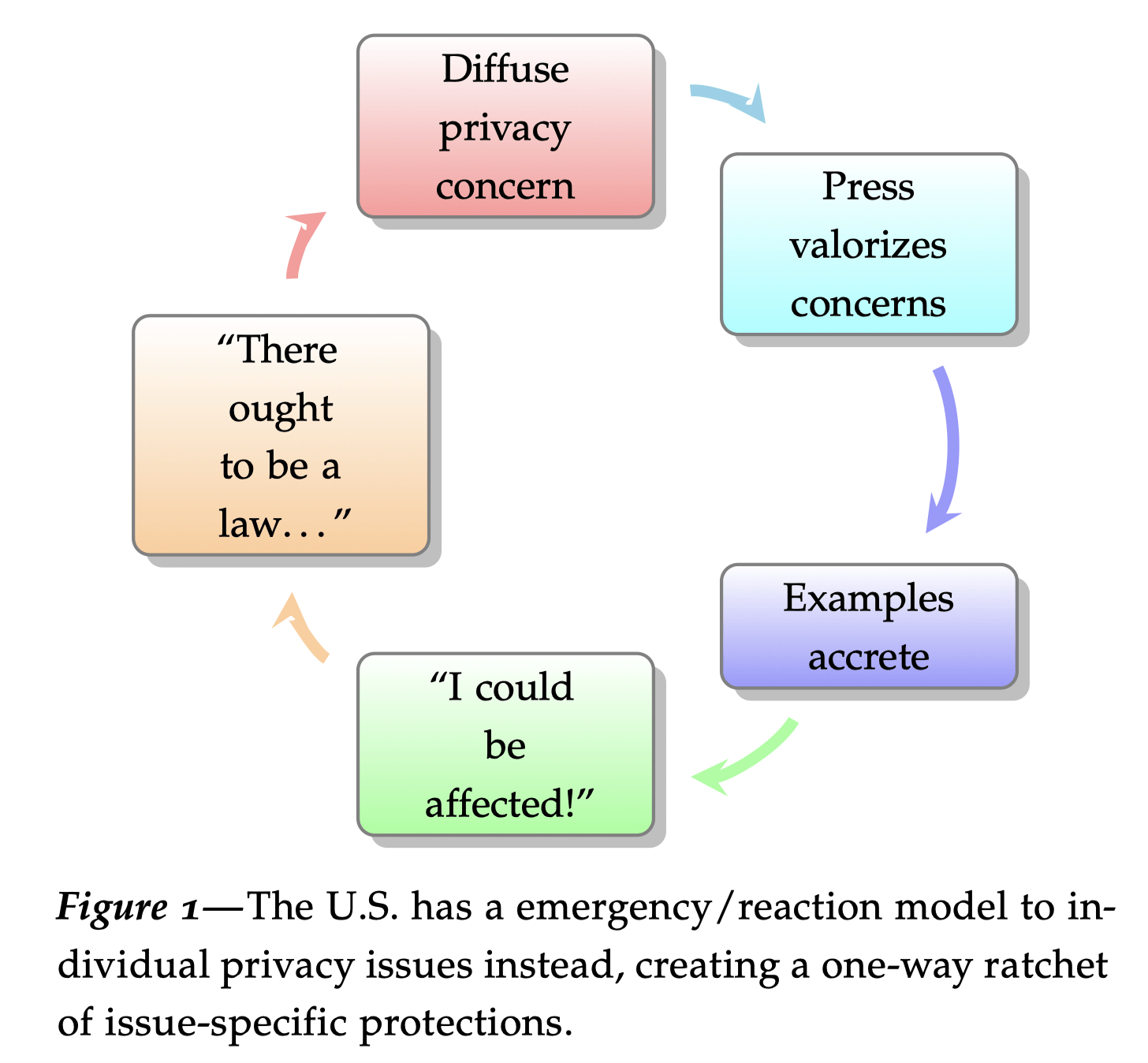
What is consumer privacy?
In this essay for a lecture at Stanford University, I attempt to explain consumer privacy as a deterrence theory strategy. I argue that privacy does have methods of analysis, based in fair information practices, while popular use of the term “privacy” is loose, a shibboleth representing uncertain values. This wide-ranging essay then goes on to…
-

The Quantum Age
Quantum technologies use quantum effects to provide some utility. These capabilities are so different from our conventional intuition that quantum technologies seem to ride the fine border between science fiction and fantasy—yet many quantum technologies can be commercially purchased today, and more are just around the corner. With Simson Garfinkel, I recently completed Law and Technology for…
-
Digital Consumer Protection
As products and services merge, we need new kinds of marketplace signals and rules to ensure that consumers understand the exchange, and so that competition is fair and vigorous. In a series of works with Case Western University Professor Aaron Perzanowski and Berkeley JSD/Yale JD candidate Aniket Kesari, we have used legal/empirical analyses to elucidate…
-
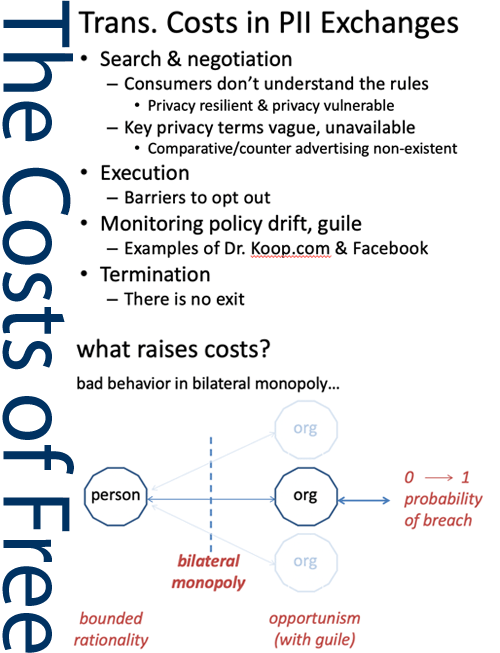
“Zero Price” != Free: How “Free” Can be Anti-Competitive
In articles with University of Washington Professor Jan Whittington (Ph.D., UC Berkeley 2008), we explore consumer-oriented internet services through the lens of transaction cost economics. This work shows how personal information transactions—“free” exchanges—can be uneconomical: consumers cannot exit these arrangements; they create lock-in; and ultimately this is a deep moat against competition. Free transactions enable companies to…
-
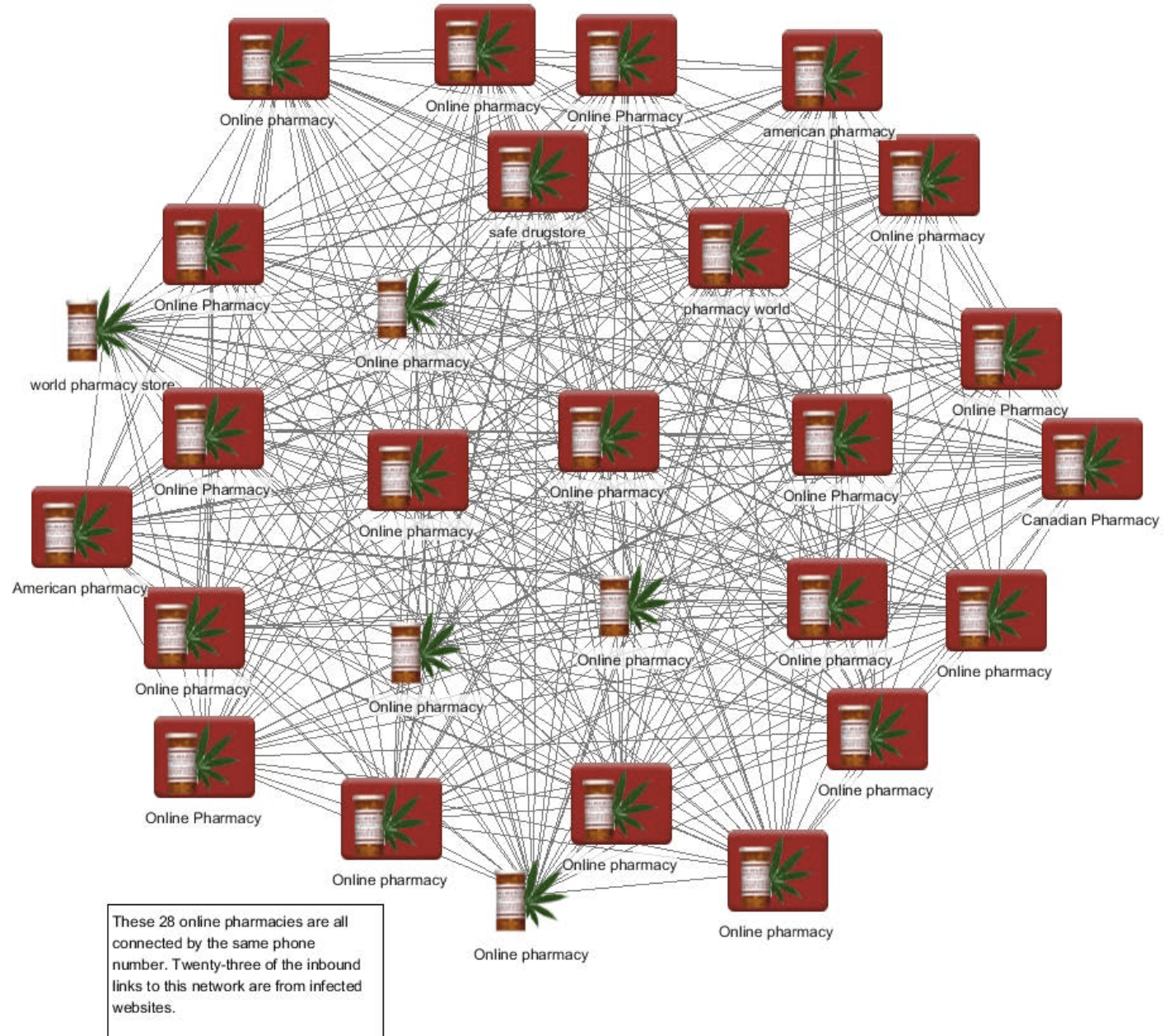
Internet Tracking & Cybercrime
We have performed terabyte-scale studies of internet tracking and of cybercrime networks, using a series of tools including Palantir Gotham, Palantir Contour, mitmproxy, STATA (Here is my STATA Cheat Sheet), Python, and a custom-built crawler. This has led to several insights, including new forms of consumer tracking in the wild (flash cookies, cache cookies), the demonstration…
-

Federal Trade Commission Privacy Law & Policy
This book is a historical account, an institutional study, and a discussion of policy choices made by the U.S. FTC. The FTC’s creation in 1914 represented a turning point in American history where skepticism of expertise and central regulatory authority was overcome by the need to address contemporary market conditions. My book connects today’s tussles over privacy…
-
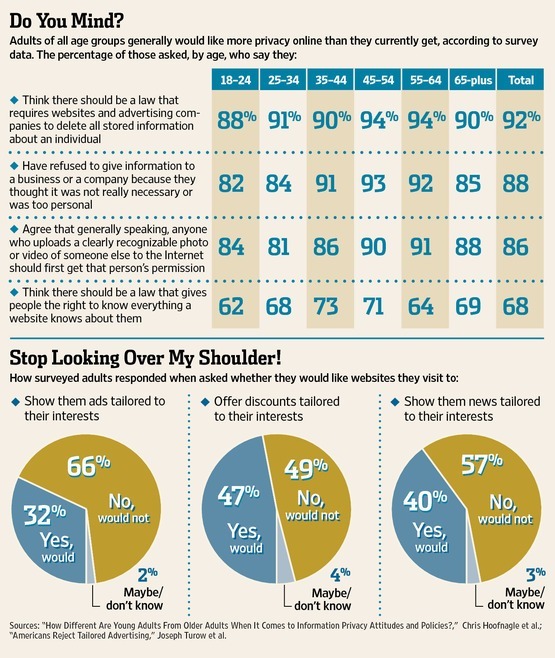
Consumer Knowledge & Attitudes
Alan Westin’s well-known and often-used privacy segmentation fails to describe privacy markets or consumer choices accurately. It describes the average consumer as a “privacy pragmatist” who influences market offerings by weighing the costs and benefits of services and making choices consistent with his or her privacy preferences. Yet, Westin’s segmentation methods cannot establish that users…
-
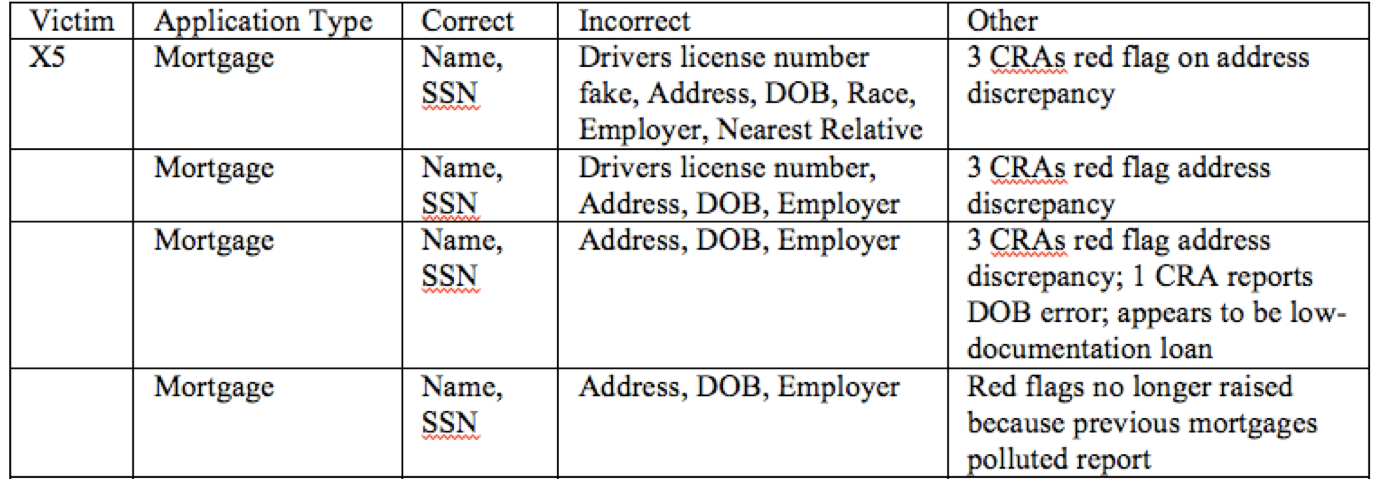
Root Causes of Identity Theft
In a trio of articles (for NSF-TRUST), I showed how identity theft is an externality of credit granting, where costs of fraud are spread among victims, merchants, and society generally. For instance, the image below is summary data on an identity theft victim who I interviewed–the impostor in the case made…
-
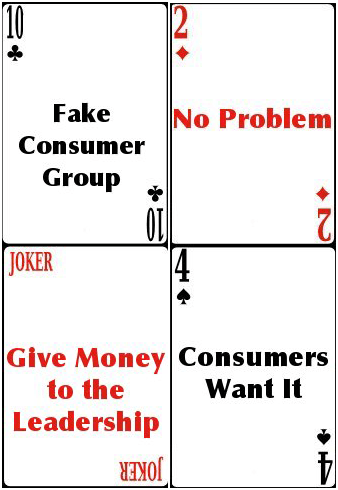
Denialism
Before coming to Berkeley, I worked in Washington, DC as a privacy advocate. I was struck by the character of policy debates there. Industries lobbied using a blend of libertarian and one-eyed public choice argument, repeating it so often that to me it sounded like simple cliché. In fact, it wasn’t debate, it was intransigence.…